ChatGPT helps Delhi man expose scammer, forcing him to beg for forgiveness
Fake payment link secretly snaps fraudster’s face, GPS location and IP address in seconds
Dubai: A Delhi man has gone viral online after he used ChatGPT to outwit a scammer, build a fake payment link that secretly captured geolocation data and a front-camera image, and then confronted the fraudster with his own photograph and coordinates — forcing him to plead for forgiveness.
The man detailed the incident in a Reddit post titled “Used ChatGPT to locate a scammer and made him beg me,” which has since sparked widespread praise for using artificial intelligence as a tool against cybercrime.
The scam attempt
The ordeal began when he received a message on Facebook from someone impersonating his college senior — an IAS officer — claiming a “CRPF officer friend” was being transferred and was urgently selling expensive home appliances and furniture at heavy discounts.
He immediately sensed something was wrong, since his real senior already had his number. When he confirmed through WhatsApp that the message was fake, it was clear he was dealing with a scammer running a classic “Army transfer/cheap goods” fraud.
Soon after, another number with an army uniform profile photo began sending pictures of items and demanding payment through a QR code, pushing aggressively for quick money.
HOW THE AI TRAP WORKED
1. Spotting the scam
A message claimed to be from a college senior, offering “Army transfer / cheap goods.” The man verified with the real person and confirmed it was fraud.
2. Fake payment page
Using ChatGPT, he generated code for a simple webpage disguised as a QR upload/payment portal.
3. Hidden functions
The code secretly included:
GPS location capture
Front-camera photo trigger
IP address tracking
4. The bait
He told the scammer to “upload the QR code here to expedite the payment,” knowing greed speeds mistakes.
5. The click
The scammer opened the link instantly — activating the tracking script.
6. Data captured in seconds
The page collected:
Exact coordinates
IP address
A clear selfie from his front camera
7. Turning the tables
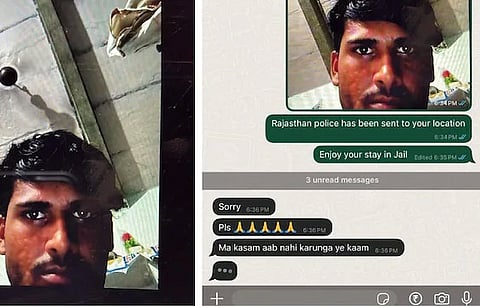
The victim sent the scammer his own image and location, leading to panic, multiple calls and frantic apologies.
Link sent
Instead of blocking the scammer, the Delhi man decided to expose him.
Pretending he was having trouble scanning the QR code, he asked ChatGPT to build a simple webpage designed to look like a payment portal but actually capture the visitor’s GPS location, IP address, and a photo using their device’s front camera.
“Within minutes,” he wrote, the AI generated functional code. He hosted the page online and sent the link to the scammer, telling him that uploading the QR code there would “expedite the payment.”
Driven by greed and impatience, the scammer clicked.
The page instantly captured his exact latitude and longitude, IP address, and a clear image from his front-facing camera — reportedly showing him seated and unaware of what was happening.
The aftermath: Panic and pleading
The Delhi man then sent the scammer his own photo and location details.
That triggered panic.
According to screenshots described in the Reddit post, the scammer immediately began calling from multiple numbers — begging the victim not to take action, promising to stop scamming and pleading for forgiveness.
“Within minutes, he went from demanding money to begging me to leave him alone,” the man wrote, adding that scammers typically switch to multiple numbers when cornered.
Although he acknowledged the scammer would “be scamming someone the very next hour,” he admitted, “the satisfaction of stealing from a thief is crazy.”
Viral reaction
Users on Reddit applauded the ingenuity.
One comment read: “AI used for the right reasons. Good work!”
Another wrote: “Mad respect. Make this open source so we can all use it.”
Others debated whether the average internet user could replicate such a setup, suggesting it might require basic IT skills despite ChatGPT generating the code.
The post has ignited a wider discussion about how AI tools are reshaping both cyber-fraud and digital self-defense in India — and whether ordinary citizens may soon have high-tech ways to fight back.
Most common scam types in India — and how to avoid them
1. Army/Police Transfer Goods Scam
How it works: Fraudsters pose as Army, CRPF, IAS or IPS officers selling “urgent transfer” items at throwaway prices.
Red flag: Uniform profile pics, urgency, emotional appeal.
Avoid it: Never pay without meeting in person. Call the real officer using publicly available numbers.
2. QR Code / UPI Collection Scam
How it works: You’re asked to scan a QR code to receive money but it actually initiates a payment from your account.
Red flag: “Scan this to get cashback/refund/bonus.”
Avoid it: Never scan QR codes from unknown numbers. Use official apps only.
3. OLX / Facebook Marketplace Courier Scam
How it works: Fake courier agents claim they’ll “send a delivery boy” and ask you to click a payment link for verification.
Red flag: Links with spelling errors, non-bank domains.
Avoid it: Deal locally, in person, cash on delivery only.
4. KYC Update / Bank Verification Scam
How it works: Caller pretends to be from SBI, HDFC, ICICI etc., threatening account freeze unless you “update KYC now.”
Red flag: Threatening tone, asking for OTP or remote screen access.
Avoid it: Banks never ask for OTP on phone. Hang up and call the official customer care number.
5. Job Offer / Work-From-Home Scam
How it works: High salary for simple work, often asking for a “registration fee” or “training charge.”
Red flag: Guarantees salary without interview or skills.
Avoid it: Never pay for a job. Genuine employers don’t charge applicants.
Fast Safety Checklist
✔ Never share OTPs
✔ Never click unknown links
✔ Don’t send money to strangers online
✔ Always verify through a known contact
✔ Trust your instincts — urgency = fraud
Sign up for the Daily Briefing
Get the latest news and updates straight to your inbox



