Dubai: Clicking a ‘like’ or ‘Follow us on Facebook’ button could lead hackers to steal your user name and password, experts warn.
A new trick has come to light in which cyber criminals use Facebook and other social networking sites to trick users into giving away log-in credentials, potentially exposing millions to identity theft.
XPRESS saw a live demonstration of how it works. The method called ‘cross-browser manipulation’ exploits vulnerabilities found in existing browsers (Firefox, Chrome, Internet Explorer) that could potentially help hackers harvest millions of user names and passwords.
Khaled Al Hawasli, 32, manager for security analysis at Help AG, gave XPRESS a demo in which this reporter’s user name and password were compromised by clicking what looked like a Facebook “Follow Us” button on the webpage of a restaurant infected with a “click-jacking” code. A page then popped up and I was asked for my user name and password after which my real Facebook page appeared. Almost immediately my user name and password was sent to Al Hawasli’s BlackBerry as an SMS message.
Al Hawasli said the same attack could be initiated in other social media sites such as Twitter and Tumblr. “This type of attack can in fact be used on any website whatsoever, but social media is more vulnerable.”
Al Hawasli said they discovered the bug about a year ago and his team will formally tell browser publishers about the vulnerability.
Facebook alone has about 1.11 billion active users as of May.
The hack injects malicious codes into a victim’s PC which is activated as per the hacker’s desired time — say 30 minutes later — to make it look like a legitimate Facebook page log-out. (This matches with a recent report by Seculert, which identifies seven million new unique malware-infected internet protocol (IP) addresses each day).
Each individual device, be it a PC, smartphone, X-Box or other video games connected to a network at any given time, have a unique IP address.
Al Hawasli, who previously worked as a cyber sleuth with the police, said these attacks are relatively new. “It uses deception. It works on eight out of 10 victims as soon as they click on a button or malware infected page,” he said.
“Hacking the site [Facebook] itself is very unlikely. But it’s the Facebook users who are not security conscious who may end up getting exploited,” he said.
Such attacks are also known as “like-jacking”, according to Taufiq Tamim of Norton MENA.
The browser vulnerability is not straightforward as it requires some degree of “social engineering” and is difficult to nail.
Social engineering involves tricking a person to unwittingly execute a code or application on the hacker’s behalf to carry out a fraud, identity theft and malicious hacking. For example, a hacker may hack a low-level employee’s account to steal sensitive information or data from a company.
Earlier this year Help AG in Dubai found a bug in business applications of Oracle, the world’s top database software company. Oracle acknowledged it and announced a patch in April.
So how vulnerable are ordinary people to such attacks?
“If you don’t have enough knowledge of how a hack works, it would be easy for you to get tricked,” said Al Hawasli.
Two hackers who turned hunters
Khaled Al Hawasli, 32, Syrian
Early days
Born in Damascus in 1980, grew up in Jeddah, Saudi Arabia, where his dad worked as a manager of a company. At age 12, he learnt to hack floppy disks by cracking the codes on unlicensed copies of computer games – basketball and computer games -- which led him to get into a spaghetti of codes, the basic building blocks of applications and games. Holds a degree in computer science, American University of Sharjah (AUS, 2001)
Current role
Manager for Security Analysis, Help AG, Dubai (four years)
On hacking
Hacking is something that grows out of interest. I didn’t have formal training. There’s no course for it.
On hackers
Hackers are here to stay. There are two kinds -- the fun-seekers and the professionals. A fun hacker brags when he makes the news and is generally harmless. The other kind is really dangerous. They hack in and steal information and nobody knows they exist. They stay invisible. Companies may hire a hackers to steal information from a competitor. It’s the same with governments. They are good at hiding their tracks.
Armando Romeo, 29, Italian
Early days
Born and raised in Crotone, Italy in 1984. Started working from age 12 for an Italian internet service provider. First used a fake mailer -- sent to his manager. At 16, he started what had become one of the world’s best-known and most visited hacking websites (hackerscenter.com), visited by up to four million per year. Formed an independent IT security research team that hunted for bugs and vulnerabilities in applications, browsers and operating systems
Current role
Chief executive officer, elearnsecurity.com
On hacking
Curiosity is a hacker’s main motivation. Fear is a nice motivator, too. If you don’t know what you’re doing, you’ll get tracked easily. An experienced person at the other end could track you down. Stealing money is a crime, whether you physically break into a bank or virtually, through the web. But if you break into your own lab as part of training, it’s not a crime. It’s like breaking your own lock at home to get in. This is hacking but not illegal. That’s what we do in training “penetration testers”, who find vulnerabilities in corporate or government sites.
On hackers
The best hackers are self-taught. Still, we founded our online training school in 2009. It’s for those who want to pursue IT security as a career. Having proper training gives you much better options. Without a learning path, you run in circles, get frustrated and give up. Training guides you through what you should know in the exact order you should know it. It increases your chances to reach your goal.
How to avoid cross-browser attack
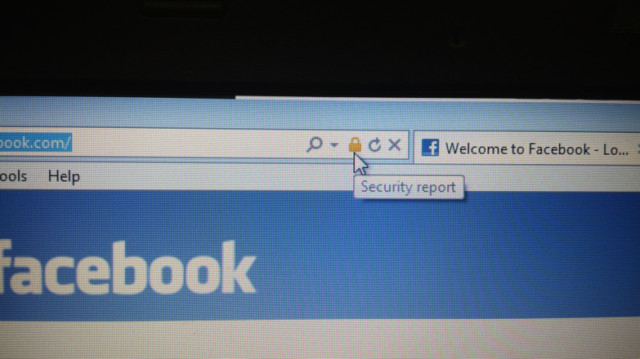
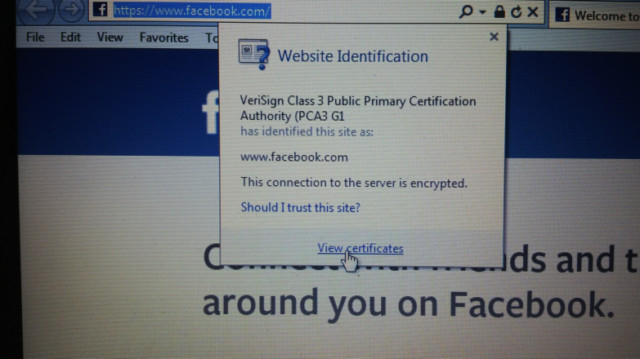
1.Make sure you are viewing a page that shows https:// (any webpage with this prefix is hard to manipulate)
2.Take these three simple steps to know when your FB page had been hacked
1.Click the “lock” item on the browser (Firefox)
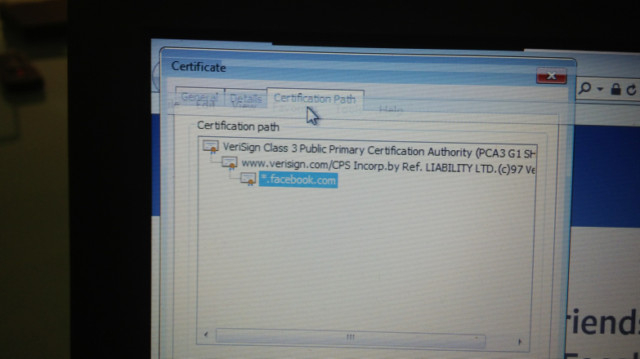
2.View Certification path
3.Make sure there’s a hierarchy (a. Verisign, b. Verisign, c. facebook.com)