Mobile devices to come under growing attack
Android attacks to become stealthier, Symantec says
Dubai: Smartphones are an increasingly attractive target for online criminals. As a result, they are investing in more sophisticated attacks that are effective at stealing valuable personal data or extorting money from victims.
Although Android users remain the main target, 2015 saw effective attacks on Apple devices as well, and iOS devices did not need to be jail-broken to be compromised.
Rayane Hazimeh, senior manager for consumer services at Symantec, said mobile threats will continue to proliferate this year. Days of PC-like exploit kits for phones commercialised on the black market is not far away.
She said both Apple and Google are working hard to secure their operating systems and wider ecosystems.
With many app stores, users are able to browse, purchase, and remotely install apps from their desktop, providing a unique opportunity for a crossover of threats.
“Recent examples of some Windows malware have exploited this by stealing browser cookies for Google Play sessions from the infected desktop computer and using these stolen cookies (essentially the users’ credentials), impersonating the user to remotely install apps onto the victims’ phones and tablets without their knowledge or consent,” she said.
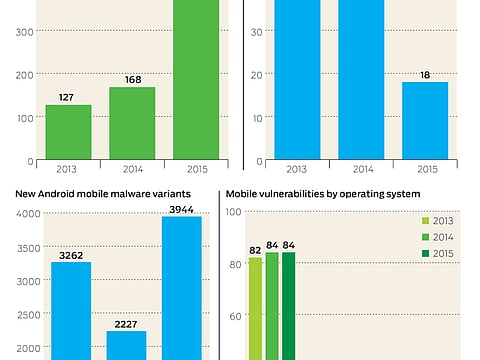
The number of “mobile vulnerabilities” has increased every year over the past three years. Unlike Android devices, iOS vulnerabilities have been a critical part of gaining access to an iOS device, especially for jail-breaking.
Jail-breaking enables a user to install apps that are not authorised on the Apple Store and bypasses the integral security of iOS.
Jail-broken devices present more opportunities for compromise and many threats are designed to take advantage of jailbroken phones. Of the 13 iOS threats documented by Symantec to date, nine can only infect jail-broken devices.
“It is much more difficult to compromise a non-jailbroken device, as this typically requires an app to be installed by downloading it from the Apple Store. Apple is well-known for its stringent screening processes, which is why the number of malicious iOS apps is so much smaller than for Android,” Hazimeh said.
However, the latest version of Android — Marshmallow (version 6.0), which was launched in October includes a number of features designed specifically to thwart attackers. According to Statista, in October 2015, KitKat (version 4.4) was still the most widely used version of Android at 38.9 per cent, and Lollipop (version 5.0) accounted for 15.6 per cent.
Jail-broken Apple devices are the focus of the majority of threats and, of the 13 iOS threats documented by Symantec to date, nine can only infect jailbroken devices.
Android malware is becoming stealthier. For example, she said that malware authors started to obfuscate code to bypass signature-based security software. Additionally, before they begin their attacks, some malware can now check to see if it is running on real phones or the kind of emulators or sandboxes that security researchers use.
The number of iOS malware threats discovered to date remains “quite small”, although it is beginning to increase, with seven new threats discovered in 2015, up from the previous high of three in 2014.
She said that the amount of iOS vulnerabilities being found annually has trended upwards over the past four years.
Between 2011 and 2014, the amount of vulnerabilities affecting iOS has exceeded those that were documented for its main competitor — Google’s Android. That trend has reversed in 2015 as so far, new Android vulnerabilities have outpaced iOS.
“The success of Apple devices has generated increased interest among attackers, as a growing number of malicious actors are developing threats for Apple platforms. The number of malware attacks against Android fluctuated during 2015. In the first quarter, we blocked approximately 550 attacks each day, the highest period of the year. This fell to approximately 272 per day by the third quarter, rising again to 495 by the end of fourth quarter,” she said.
Besides familiar tricks such as hiding malicious code inside ostensibly legitimate apps, or being disguised as something more useful, she said that attackers are using more sophisticated techniques to make money from their victims.
For example, Symantec researchers uncovered a new Android phishing Trojan that tricks users into entering their banking credentials by popping up a fake login page on top of legitimate banking apps. Similarly, she said that the latest Android ransomware copies Google’s design style to make it appear more legitimate and intimidating when it displays fake FBI warnings on users’ lockscreens.
“We have also seen phone ransomware start to encrypt files, such as pictures, rather than simply change the phone’s access PIN,” she said.
How to protect mobile devices
• Treat mobile devices like the small, powerful computers and protect them accordingly, including access control, including biometrics where possible.
• Data loss prevention, such as on-device encryption.
• Automated device backup.
• Remote find and wipe tools, in the event of a lost device.
• Refrain from downloading apps from unfamiliar sites and only install apps from trusted sources.
• Don’t jailbreak devices. Jailbroken devices are often more susceptible to security issues.
• Only install software from reputable sources. Some third-party OS X app stores have been found to host Trojanised software. Grayware, such as adware, and potentially unwanted or misleading applications are often bundled with installers for other applications.
• Delete any suspicious-looking emails you receive, especially if they include links and/or attachments. Don’t even open them, just delete them. If they purport to come from legitimate organisations, verify with the organisation in question first.
• Pay particular attention to permissions requested by an app.
• Update apps as often as possible, or if a suspicious app is identified, delete it and wait for a new version to be made available.
• Change your Apple ID password, or your Google Play password, if you suspect your account has been compromised. This advice extends to safeguarding account credentials on any third-party App Store.
• Watch out for any suspicious emails or push notifications to your device asking for your credentials, or any other personally identifying information.
• Until a patch is applied, proceed cautiously when using your mobile browser to preview unsolicited audio and video files.
• Android users are advised to apply any security updates issued by their carrier or device manufacturer as they become available.
• Additional mobile security solutions can also help safeguard against malicious software, and enterprises should consider mobility management tools that can help secure and control mobile devices within an organisation.



