
Highlights
- Easy-to-guess passwords (123456) are the root cause of a number of cyberattacks.
- Businesses have not removed them from the authentication process.
- Even two-factor authentication is not air-right, as there are at least 5 ways it can be breached.
- Know what's behind the spike in 'social engineering' attacks.
An estimated 300 billion passwords are used by humans and machines worldwide. That’s far too many passwords — 40 times more than the number of people walking on planet Earth. The more the number of passwords, the higher the number of breaches: In the first half of 2020, data breaches exposed 36 billion records, according to RiskBased Security, a US-based cybersecurity firm specialising in vulnerability intelligence, data breaches and risk ratings.
What’s the salvation for a password-weary world? There are no quick answers. It's a frustrating fact: Many people have grown weary of passwords; yet until now, there’s not much left in terms of choice. The world has become so accustomed to the necessity of passwords. They’re the entry point to the digital world, which gives every user a semblance of ownership.
Why do we mess up with passwords?
The whole of humanity is familiar with passwords. As a rule, no two passwords should be the same. Our dependence on them is intertwined with digital technology use, like we need nappies for babies. We use passwords to check our email, log in to our social networks and browse our mobile phones, watch movies, transact with our bank, etc. A password helps tell the system that we are who it "thinks" we really are. Yet, we all know that passwords, like nappies, aren't always foolproof. "Human factor" kicks in. And we all know that in every adult hides a "child within". Then it's a big mess.
• This data point held true in 2017. A similar report, published in 2019, showed that not much has changed.
So are passwords really 'dying'?
Instead of being a cause of comfort, however, passwords had caused despair. Don’t even start asking about desperate parents who forget the password of their children’s iPad, linked to an iCloud account. When that happens, the iPad becomes as good as a doorstop.
The 2 iPads were completely disabled. No one in my family could remember the iCloud details that would enable us to unlock them. Calls to Apple service centre came back with the same advice: log in to iforgot.apple.cơm, which referred us back to iCloud. It was painful, frustrating. For months, I must admit, those 2 tablets were a constant reminder of our negligence. That is, till I found a small hole-in-a-wall shop who had some sort of a hacker among their staff...and sorted it for us. [JH]
And we all know that in establishing security, passwords are not perfect either. Cyber hacks and ransomware attacks have increased, despite the increasing sophistication of passwords. Such attacks are only bound to increase, say experts. Is man’s love-hate affair with passwords about to be disrupted?
I think password is dying… simply because organisations find it more difficult to maintain passwords, as it has a lot of administrative overhead, both for IT (department) and end-users.
“I think password is dying… simply because organisations find it more difficult to maintain passwords, as it has a lot of administrative overhead, both for IT (department) and end-users,” said Anoop Kumar Paudval, Information Security Manager of Gulf News.
Passwords are seen as belonging to one’s unique — and personal — space. We’re supposed to keep them and remember them by heart. Most of the time, we do (or don’t), depending on our amnesia level. But as our digital technology/media use increases, panic attacks driven by I-forgot-my-password episodes have also increased.
The next step in this evolution: password managers. Instead of reusing the same password for different accounts, you only enter a “master password” — which then works to log in across your social media, banking and other productivity apps.
For Mac users, there’s the “Keychain” too, Apple's password management system for the MacOS (first came out in OS version 8.6), and has been included in all subsequent versions. A Keychain can contain various types of data: passwords, private keys, certificates, and secure notes.
And while using a Password Manager or Keychain is safe, it has one downside: trouble comes if you forget the master password.
Passwords are meant to be remembered, but this makes them predictable. Because characters form the basis of passwords, there's also no perfectly unique password. And whether we like it or not, passwords are the root of all hack attacks.
Passwords are the inherently weak link between security policies and the end-users. Hackers know this. Therefore, they exploit this vulnerability to the hilt, with ever-increasing "social engineering" attacks (explained below).
What is 'password fatigue'?
Passwords are a very personal, secret-agent kind of thing. When you forget them, you can’t just ask an officemate, a neighbour or even an IT support guy “What’s my password?” It sounds absurd at the very least, and irresponsible at the very most.
When you try — and repeatedly fail — to log in to your account for the nth time, 'password fatigue' becomes a catchphrase of despair. And don’t even dare to ask your spouse. Whether s/he knows it or not, it’s bound to cause frustration to either side — or both.
Consider this: It’s become a standard practice for most organisations to force a password change among users every so often. For some, it’s once every three months, or 4 passwords to note down in one year — equivalent to 40 passwords in 10 years and 160 passwords during one’s working lifetime (considering the average working life of 40 years).

As the number of passwords end-users must have keeps piling up, password pain only intensifies. That’s part of the reasons why password management software has grown so much. According to SecureAuth's survey, 1 in 3 IT security professionals report that their users inundate help desk due to frequently forgetting passwords.
Is it a good practice to keep a log of your passwords?
It is. Many people keep a written log of passwords on a separate notepad, to help them remember access to apps or sites. While this works for many, it’s not 100% perfect. Most people, in order to avoid password anxiety or fatigue, simply just use — and reuse— the password they’ve been given by IT.
What if I re-use a password?
Here’s one problem: with too many unique passwords to handle — which is more than human nature allows us to possibly remember — people do get lazy, and reuse password all the time. The result: easy-to-guess credentials being employed. In 2019, the most commonly hacked password was “123456”, according to the UK’s National Cyber Security Centre. Ergo: as much as 81% of company data breaches is due to having poor password practices, according to cybersecurity firm TraceSecurity.
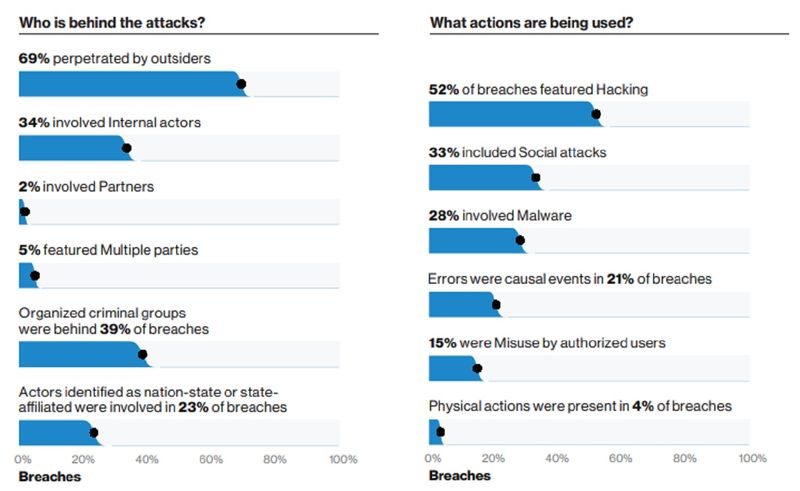
Besides passwords, what are the ways of authenticating people digitally?
While it’s a fact that easy-to-guess passwords are the root cause of a number of cyberattacks, businesses have not removed them from the authentication process – instead, what is known as “two-factor authentication” has been introduced.
Companies are trying to find ways of authenticating employees using the following:
USE 2-FACTOR AUTHENTICATION: In most companies, this approach involves an individual needing two of the following pieces of information before their identity is verified: something they know, something they have, and something they are.
SOMETHING PEOPLE KNOW: In the case of something people know, a password remains the most commonly-used piece of data. Something they have might be a device, like a smartphone, and something they are might include biometric data. This extra layer of security makes it much harder for hackers to access digital or business assets.
USE A PASSWORD MANAGER: Password managers are applications that store information for multiple digital solutions and log in users automatically. They hold a database of passwords that is encrypted and can only be accessed via a master password. This works for many, as it leaves users with much less to remember. This also indicates that less likely to use 123456 and more likely to choose a stronger password overall.
Even two-factor authentication is not air-right, as they can be breached. One is through what is known as the widely reported “SIM card swap”, where the one-time password sent via SMS can be stolen.

How does 2-factor authentication work?
It’s an identification system that always requires an added security "layer”. The first factor (when logging in to an account): enter your username and password. Second factor (if 2FA is enabled): You provide a second form of proof that you are the owner of the account before you can access it (such as fingerprint, face or iris scan, or one-time password).
Why do you need 2-factor authentication?
The idea is that, if by some accident or unguarded moment, you gave away your password (say, to a ‘phishing' attacker), hackers would need to get access to the second form of identification before they could enter your account. Experts recommend that as much as possible, you must turn on two-factor authentication essential accounts. This extra layer of security doesn’t hurt, and keeps you secure — for the most part. Unless, of course, you fall victim to social engineering, and you give away the two-factor authentication code yourself.

What are the most common authenticator apps?
Following are some of the more common smartphone apps you may consider:
- Google Authenticator
- Microsoft Authenticator
- Salesforce Authenticator
- SecureAuth
- Duo Security
- Symantec VIP
- Transakt
- LastPass Authenticator

Is two-factor authentication safe?
Any layer of security is always better than just a single layer (password). 2FA is one of the best ways to add a secruity layer. But if you think that since you have enabled or implemented two-factor authentication (2FA), you’re hack-safe — think again. The website hoxhunt.com has listed five ways this layer can be breached/bypassed:
- Via conventional session management
- Using OAuth
- Using brute force
- Using earlier-generated tokens
- Using social engineering
It is also commonly known as “hacking the human” — because it involves manipulating human beings to provide sensitive information or sensitive details.
What are examples of social engineering attacks?
- “Phishing” attacks, where victims are tricked into providing confidential information;
- “Vishing" attacks where an urgent and official-sounding voice mail convinces victims to act quickly or suffer severe consequences;
- “Physical tailgating attacks” that rely on trust to gain access to a network.

How easy would it be to switch over to biometrics?
While many experts say the era of passwords seems to head towards the same destiny as the dinos, getting people to switch to something else (biometrics) might not be a walk in the park. The world’s experience with passwords is undergoing a major challenge. Some say it is likely to be a “slow death” for passwords.
How much does it take to curb such breaches?
There's pressure to push back hackers, but it comes at a price. The average cost of a data breach is $3.86 million as of 2020, according to Varonis. To counter such threats, the global information security market is forecast to reach $170.4 billion in 2022, according to a Gartner report.

Where does human error come into play?
According to Cybint, 95% of cybersecurity breaches are caused by “human error”. Inadequate password protocols is responsible for a sizeable chunk of this figure.
155.8 m
estimated number of individuals affected by data exposures in 2020Are biometrics the way to go?
The answer to this is another question: Which one is better — remembering 20 different passwords or transitioning to a better, more robust system of authentication? The answer is pretty obvious. But the solution and reality is always more complex and not so straightforward.
Most IT professionals believe passwords won't exist in 10 years. This prognostication, however, has been on for well over a decade already. For example, in 2004, Microsoft founder Bill Gates said said passwords are on the way out. Many IT professionals, too, believe the same way. And while we’ve seen the risk with passwords, deciding what to replace them with is a huge challenge. And while it’s true that biometric identification – like a fingerprint or an iris scan – is harder to hack, the consequences of being able to do so are much greater.
What are the alternatives to use of password?
Since Bill Gates’ end-of-password prediction in 2004, numerous two-factor authentication and biometrics products have literally flooded the market. They supposedly heralded the end of the password using the following:
- Dongles
- Soft tokens
- Digital fingerprint
- Facial recognition
- Palm vein readers
- Iris recognition
- Keystroke dynamics
But while these alternatives came and went, the password has remained as firmly entrenched as ever.
NUMBERS
$ 18.78 b
Value of the biometric security market in 2020 (apart from the bigger global IT security market): Frost & Sullivan report
Why do hackers aim at biometrics?
It's simply because they’re high-value targets — getting a hold of not just passwords, but also fingerprint, iris scan and facial scan data of people is valuable to the Dark Web hacking community. For one, copies of biometric information stored and used by organisations and companies to verify each individual makes them attractive targets for ransomware attackers looking to “harvest” credentials. When a password is compromised, they can be changed. A fingerprint, or iris scan, cannot.
SOFTWARE AS A SERVICE?
Software as a service (SaaS) apps and mobile services growth, password prevalence is growing. The global password management market is growing at a robust annual rate of 16.33%, according to a Research and Markets report.
security spending on biometrics technology by 2024: Frost & Sullivan report
Phones that use facial recognition: Where do they fit in?
With the built-in use of biometrics (on iPhones and some Android phones, for example), and Apple's use of biometric authentication into its Apple Pay service, these are signs biometrics are going mainstream. Soft token authenticators and other software-based mobile authentication tools have added a layer of security and are easily available due to smartphone ubiquity.
$ 45.96 b
estimated value of security spending on biometrics technology by 2024One way of knowing the shape of things to come is to follow the money. With the rise of Internet of Things (IoT) and smartphones, security spending on biometrics technology rose from around $3 billion in 2008 to $7.3 billion by 2013, to $18.78 billion in 2020. By 2024, this could grow up to $45.96 billion, at a compound annual growth rate of 19.6%, according to a Frost & Sullivan report.
_conference_resources1_16a4a164c05_original-ratio.jpg)
Are we then witnessing the rise of biometrics?
A survey from Wakefield Research and SecureAuth shows the answer is “Yes” from most IT practitioners. At the current rate authentication and authorisation technology is progressing, they believe passwords will be passe in 10 years. Among the 300 IT decision-makers surveyed, 91% agree that the traditional password will not exist in a decade, the survey shows. Approximately 66% of IT professionals said they are already using authentication methods beyond passwords. Whether these predictions happen or not, only time will tell, come 2031.








